
Jan 22, CISA posted a PR video on X of all the wonderful advances they had made in 2023. The big push was getting companies to use 2FA and implement PCI-DSS.
Today(1/31) Director Wray issued a warning that China was about to attack the US infrastructure, and in congressional hearing, Jen Easterly, director of CISA, testified that CISA is coordinating with FEMA, while Republicans were vilified for cutting CISA budget by 22%.
I think it is ironic that both X and the US Government will not text to my phone numbers, making 2FA impossible. Every business and carrier can send texts to me (even TruthSocial can), so it made me question what carrier/service are they using that blocks the US Government’s ability to text me.
My run-in with PCI-DSS was with US Bank’s Elavon merchant services who required establishing policies for non-existing technical staff, and insisting on a British “agency” to perform penetration testing which could only succeed if I turned off the CidrPress™ security system. (Information collected was then exploited – and failed – hacking from numerous Baltic states.)
A week ago, in a LinkedIn post, I posted some comments with regard to #cybersecurity misdirection including the BS around #pcidss and X’s and USGov’s trouble with 2FA. As usual that brought a firestorm of hacking attempts on SohoStar’s servers
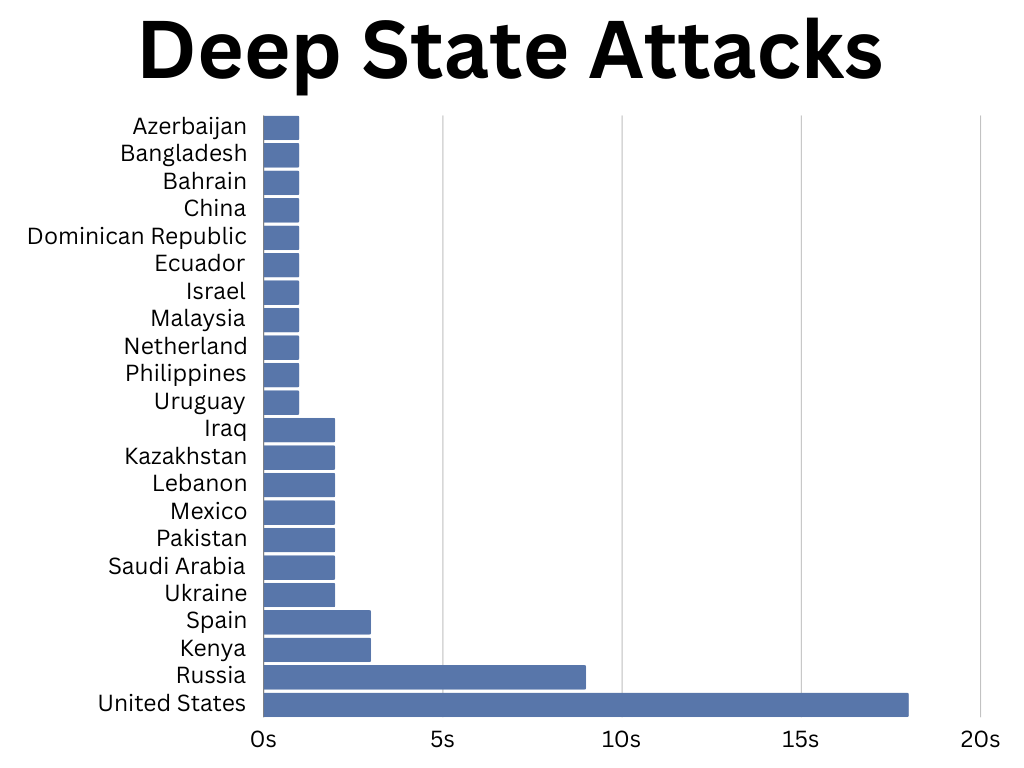
That night, CidrPress™ observed some interesting activity.
Normally, CidrPress sees a series of similar attacks bouncing from country to country, login attempts for women’s names for example, from Pakistan, then Viet Nam, then Turkey.. and so on. Sometimes multiple scripts get run that cause overlaps for a second.
That night I had multiple “blocks” of attacks occurring from multiple countries in exactly the same second. Do you realize the coordination required to have 7 attacks at the same second, from many diverse countries? When I analyzed the countries and IP record I was surprised to find that many names were familiar:
Amazon Technologies, Charter Communications, Comcast Cable, Google, Microsoft, New Wave Communications, Oracle, PSINet, T-Mobile, The Constant Company, Unified Layer, Unus, Vultr Holdings
These are names associated with the US Government due to their prominence on our network backbone. Of all cyber secure systems, these players don’t get hacked. Period. This was an inside job.
Many of the non-US attacks used un-assigned IP addresses (Internet infrastructure belonging to RIPE, APNIC, and LACNIC), making it even harder to believe this could have been random hackers misusing under-protected PCs.
This is not uncommon to feel the penetration testing and hacking after openly challenging a CyberSecurity agency, or global social media platform. Postings about CidrPress™ performance always attracts gunslingers who come to challenge the Sheriff. This wasn’t a random hot-shot, but an intentional campaign using US infrastructure assets.
The question then is who do you go to, when a Government that is supposed to be protecting you from enemies, Foreign and Domestic must be behind incidents, or should I believe that the US infrastructure is SO F*cked up to be grossly incompetent when implementing ZeroTrust in accordance with Executive Order 14028, “Improving the Nation’s Cybersecurity”?
I have a number of well connected contacts with security clearances, and I know from experience that the US infrastructure is robust and that critical components of our defense are not open on the Internet.
With FBI Director Wray’s warning, and the testimony of Jen Easterly, this is clearly a false flag operation to destabilize and distract from a number of news worthy stories, such as Mayorkas’ impeachment, border invasions, and the rise of Trump again.
It is bad enough that foreign agents constantly attack US businesses, It’s something completely different when attacks come from the government colluded – major US tech who should be the pinnacle of defense; shame on them.